In his groundbreaking book In Praise of Slow, Carl Honoré championed the idea that taking a more deliberate, thoughtful approach to life often leads to better outcomes. From the slow food movement to mindful work practices, the lesson is clear: haste can be costly. This principle applies just as aptly to software development and package management.
The Perils of Rushed Updates
The software community has recently witnessed the dangers of hasty updates. A sophisticated supply chain attack compromised the popular NPM package @ctrl/tinycolor, which boasts over 2 million weekly downloads. The malware spread rapidly, leveraging the package's widespread use to infect other projects. Despite its sophistication, the open-source community detected and neutralized the threat within hours, highlighting the power of vigilant developers and collaborative security practices (source).
The Risk of Regression Bugs
While rapid updates can introduce new features and fixes, they also carry the risk of regression bugs - issues where previously functioning features cease to work as intended. A study of the Linux kernel found that, on average, regression bugs were fixed in less than a month, but this timeframe varied significantly depending on the subsystem and complexity of the code (arxiv.org).
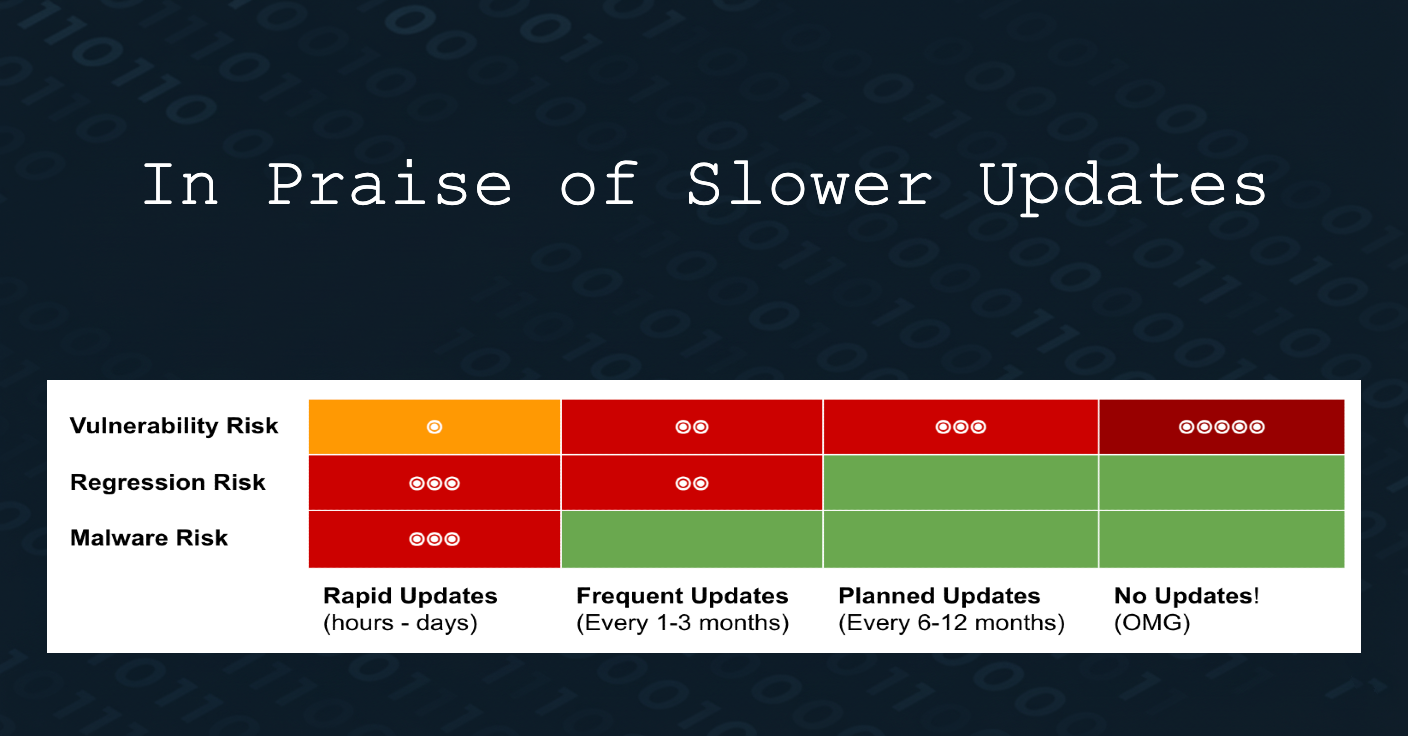
For open-source packages more generally, the time to detect and resolve regression issues is often longer. A research studying 6 major open source projects, finds that ~60% of the issues are discovered and fixed within 3 months. Factors such as package complexity, maintainability, and usage patterns can extend this period, and it is common for developers to only be confident that a specific package version is free of regression problems after six to twelve months. This underscores the value of a measured update cadence, allowing time for real-world usage to surface hidden bugs before they affect production systems.
The Longevity of Vulnerabilities
Studies have shown that vulnerabilities in open-source software can persist for extended periods before being addressed. A large-scale empirical study found that the average lifetime of a vulnerability is around four years, varying significantly between projects - approximately two years for Chromium and about seven years for OpenSSL (usenix.org). This prolonged exposure increases the risk of exploitation, especially when updates are rushed or infrequent.
The Sweet Spot for Updates
Given the longevity of vulnerabilities and the risks of rapid updates, a balanced approach is essential. Updating dependencies at a measured pace - neither immediately nor too delayed - allows time for regression bugs to surface while ensuring critical vulnerabilities are addressed. A cadence of six to twelve months often represents a practical sweet spot for many production systems, if only security issues discovered during this period could be handled easily.
Conclusion
The mantra of "slower is better" holds significant value in software development. By adopting a more deliberate approach to updates and leveraging strategies like backporting, developers can enhance both security and stability. While exploits can happen in minutes, not every update needs to be rushed - careful planning and measured update cycles help teams avoid introducing new problems while keeping systems protected.